What is Cloud Computing? Part 8 – Cloud Security
Is the Cloud Secure?
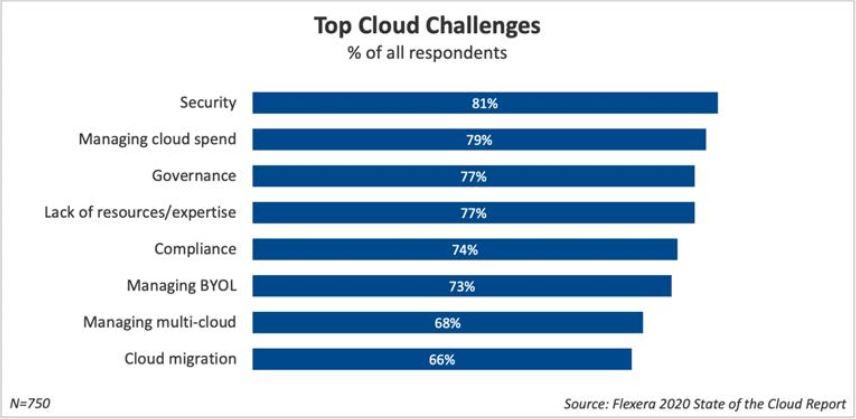
According to the Flexera 2020 State of the Cloud Report, Security remains the top concern of enterprises thinking about moving to the Cloud. This isn’t all that surprising.
Intuitively, the idea of storing your company’s data and running mission-critical applications in a location beyond your organization’s physical control seems like a risky proposition. But the truth is, cloud based systems are often more secure than their on-premises counterparts.
The major Cloud Providers hire top security professionals to constantly monitor and improve their security capabilities. Starting with their data centers, these Providers have state-of-the art physical security and develop rigorous security policies for their employees and vendors to follow. They routinely perform 3 rd -party audits and hold themselves to very high standards. For most small and medium sized business, it is difficult to match this level of physical infrastructure security.
Okay, so maybe the data center is really secure. But what about the virtual servers and the applications that run on them?
To appreciate the high level of security for these virtual assets, let’s consider the Amazon Web Services (AWS) concept of “shared responsibility”.
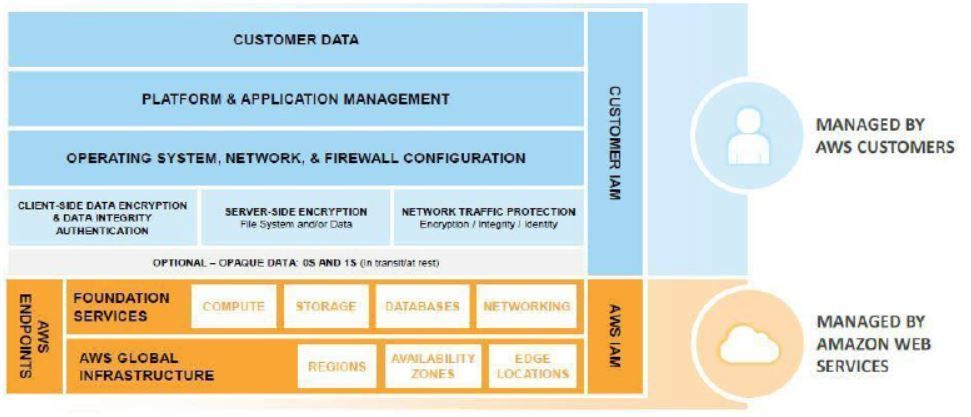
The shared responsibility model requires AWS and customers to work together towards security objectives. Within this model, AWS provides a secure global infrastructure while the customer is responsible for:
- Operating Systems
- Applications
- Data in Transit
- Data at Rest
- Policies and Configuration
These are the same assets and processes that a customer would be responsible for in an on-premises network environment.
Because AWS understands how difficult it is to secure these assets, they’ve created a sophisticated management platform with powerful configuration tools to manage and control which Cloud resources users can access.
AWS also provides tools that customers can use to create virtual private clouds (VPCs) to separate their assets from those of other customers. VPCs can be fortified with firewalls for both virtual servers and applications to protect customer assets from malicious attacks. In addition, VPN services can be used to build encrypted tunnels for secure data transmission between the Customer premises and the Cloud. Finally, AWS provides tools to encrypt all customer data wherever it is stored in the Cloud.
These are just some of the tools that AWS offers to assist its customers in building a secure Cloud environment. When combined with enhanced logging and monitoring tools and a multitude of automated backup options, the AWS Cloud offers one of the most secure computing environments in the World.
Other major Cloud providers have architectures that are similar to AWS. Working with a reputable Cloud integrator who understands how to utilize the available security tools, Customers can be confident that their Cloud environments are safe and secure from external threats.
Network and application security is a major concern for every company connected to the Internet (that pretty much includes all of them). And it is hard to imagine a more secure computing environment than those that are offered by major Cloud Providers like AWS.
Join us for the next installment of our “What is Cloud Computing?” Blog series when we explore Managing the Cost of Cloud Services. Until next time!





Browse Our Website
Contact Information
Phone: 972-675-5400
Email: info@red1ns.com
Address: 4310 Wiley Post Rd Ste 202E Addison, TX 75001
License Info: B07288701

